California Cybersecurity Integration Center

- Transparency in Frontier AI Act Reporting
- About Cal-CSIC
- Cal-Secure
- ESF 18
- State and Local Cybersecurity Grant Program
- California Cybersecurity Task Force
- Reporting
- Resources
Click here to Report (link coming soon)
In the interim, please submit all Transparency in AI Act related reports by calling or emailing:
Cal-CSIC at (916) 636-2997 or calcsic@caloes.ca.gov
Transparency in Frontier Artificial Intelligence Act (TFAIA)
Background
California is leading the world in artificial intelligence innovation and research through companies large and small and through the state’s remarkable public and private universities.
Artificial intelligence, including new advances in foundation models, has the potential to catalyze innovation and the rapid development of a wide range of benefits for Californians and the California economy, including advances in medicine, wildfire forecasting and prevention, and climate science, and to push the bounds of human creativity and capacity.
While the major artificial intelligence developers have already voluntarily established the creation, use, and publication of frontier AI frameworks as an industry best practice, not all developers are providing reporting that is consistent and sufficient to ensure necessary transparency and protection of the public. Mandatory, standardized, and objective reporting by frontier developers is required to provide the government and the public with timely and accurate information.
Transparency in Frontier AI Act Reporting
The above link will direct you to the Governor’s Office of Emergency Service’s reporting portal where members of the public and frontier developers can confidentially submit the following reports required under the Transparency in Frontier Artificial Intelligence Act.
- Critical safety incidents.
- Periodic summaries of any assessments of the potential for catastrophic risk resulting from internal use of frontier models.
Collective safety will depend in part on frontier developers taking due care in their development and deployment of frontier models proportional to the scale of the foreseeable risks. For more information on the Transparency in Frontier Artificial Intelligence Act, please reference the full bill text here.
Business and Professions Code section 22757.12(d): A large frontier developer shall transmit to the Office of Emergency Services a summary of any assessment of catastrophic risk resulting from internal use of its frontier models every three months or pursuant to another reasonable schedule specified by the large frontier developer and communicated in writing to the Office of Emergency Services with written updates, as appropriate.
Mission
The California Cybersecurity Integration Center’s (Cal-CSIC) mission is to reduce the number of cyber threats and attacks in California. The Cal-CSIC’s focus is to respond to cyber threats and attacks that could damage the economy, its critical infrastructure, or computer networks in the state.
The Cal-CSIC is the hub of state government’s cybersecurity events. The Cal-CSIC will coordinate information sharing at all levels of government agencies, utilities and other service providers, academic institutions, and nongovernmental organizations.
The Cal-CSIC will publish a statewide cybersecurity strategy. The strategy will take recommendations from the California Task Force on Cybersecurity and follow state and federal requirements. The cybersecurity strategy will improve how cyber threats are found, understood, and shared. The strategy will strengthen cyber emergency preparedness and response, standardize data protection measures, enhance digital forensics, and increase cyber investigative capabilities, supply lessons learned to California’s workforce of cybersecurity professionals, and expand cybersecurity awareness.
The Cal-CSIC will supply a Cyber Incident Response Team to serve as California’s primary unit to lead cyber threat detection, reporting, and response to public and private entities across the state.
The Incident Response Team will aid law enforcement agencies with jurisdiction for cyber-related criminal investigations and work with agencies responsible for advancing information security within state government.
Cal-CSIC information sharing will protect the privacy and civil liberties of individuals and preserve business confidentiality. Cal-CSIC will publish Cyber Threat Alerts and Advisories that will supply cybersecurity threat information between Federal, State, Local, and Tribal government entities. Advisories and Alerts are shared with private sector partners.
Cal-CSIC Analysts will collect and analyze phishing emails to document relevant information about the attacker and the Indicators of Compromise (IOC). These IOCs are added to the California Automated Indicator Exchange and is accessible to all partner entities.
Cal-CSIC Commander (Acting)

Matthew Sage
Current duties of the Cal-CSIC Commander include:
- Work with multi-jurisdictional stakeholders
- Manage interdisciplinary teams charged with safeguarding information technology assets and cyber networks.
- Maintain in-depth knowledge of state-of-the-art cyber defense strategies and mitigation efforts, including hardware and software, and network protection configurations.
- Maintain knowledge of homeland security strategies, particularly with respect to California, and their interrelationship with cyber security policy
- Develop and execute Budget Change Proposals
The California Cybersecurity Integration Center is composed of 3 branches that mutually support the Commander’s mission.
Cyber Operations Branch Services
- Incident Response
- Reactive
- Rapid Response
- Threat Identification
- Threat Containment
- Threat Eradication
- Rapid Response
- Proactive
- Security Assessments
- Network Perimeter Vulnerability Scan
- Dark Web Review (Credentials & Data Dumps)
- Net Flow Traffic Analysis
- Free 30-Day License for an Endpoint Detection and Remediation Tool
- Security Assessments
- Reactive
- Digital Forensics
- Hard Disk Forensics
- Memory Forensics
- Network Forensics
- Malware Analysis
Cyber Threat Intelligence Services
- Tactical
- Intelligence Collection and Analysis
- Intelligence Aggregation
- Intelligence Origination
- Cyber Threat Analysis
- Intelligence Governance
- Vulnerability Analysis
- Attack Surface Reduction
- Network Footprinting
- Cyber Risk Analysis
- Prioritized Vulnerability Reporting
- Critical Vulnerability Patch Validation
- Intelligence Collection and Analysis
- Strategic
- Planning and Coordination
- Dissemination
- Intelligence Objective Prioritization
- Intelligence Collection Planning
- Planning and Coordination
Mission Support Branch
The Mission Support Branch (MSB) provides internal technology and administrative resources in support of Cal-CSIC operations. MSB’s internal functions include:
- Cyber Policy and Strategy Generation
- Knowledge Management
- Vendor Management
- Product Support
- Relationship Management
- Partner Integration
- Onboarding and Partner Success
- IT Engineering
- IT Project Management
- System Engineering and Development
- Metrics Collection and Reporting
- IT/Cyber Investment Management
- Metrics Reporting and Governance
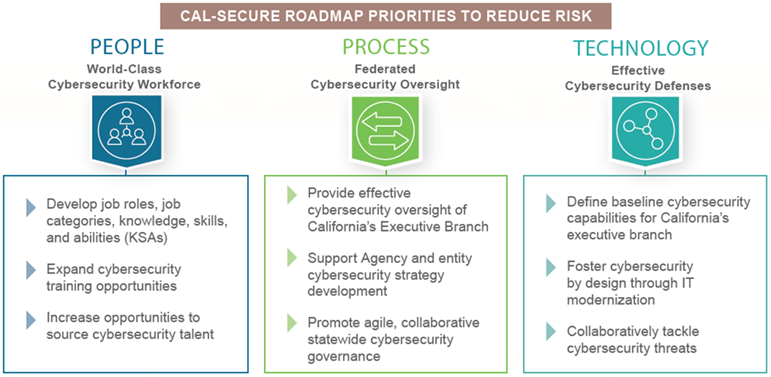
In early October 2021, The California Department of Technology (CDT) announced Cal-Secure. At its core, Cal-Secure is a five-year information security roadmap designed to increase cyber resiliency amongst California State Agencies. It implements a process that results developing a world-class cybersecurity workforce. This effort will bring people, processes, and technologies together in a joint and cohesive effort to increase the cybersecurity protective posture for the State of California.
The purpose of this Emergency Support Function (ESF) #18: Unified Cyber Command Annex is the following:
- establish a unified understanding of key cyber concepts and terminologies
- provide a system to evaluate the severity of a cyber incident
- assign roles and responsibilities to City stakeholders
The plan is specifically focused on priority SEVERE or EMERGENCY cyber incidents, when the City’s Emergency Operations Center (EOC) is activated to coordinate:
- key processes for sharing threat intelligence
- develops situational awareness
- manages operational response in a cyber- disrupted environment
Scope
ESF #18: Unified Cyber Command Annex plan addresses cyber incidents that have or could potentially degrade, damage, or destroy information systems in City Departments, Agencies, Offices, and Commissions. High focus will be given to cyber incidents affecting City government critical functions and infrastructure, including:
- Medical/Healthcare Services
- Government/Public Safety Services
- Financial/Banking Services
- Transportation/Transit Services
- City’s Telecommunications Services
- City’s managed Lifelines – Critical Infrastructure
- City’s Radio Infrastructure
- City and Department IT Networks
- City and Department Enterprise Technology and Applications
Unified Cyber Command Incident Response Process
| Phase | Objective |
|---|---|
| 1. Preperation | Identify activity or work that should be completed to make the response successful |
| 2. Reporting and Detection | Provide channel to report suspected incidents and verify that an incident has occured |
| 3. Analysis, Notification and Detection | Understand the incident and begin notifications and escalations |
| 4. Containment | Stop the incident from spreading further and eliminate further damage |
| 5. Eradication | Determine the root cause and fully eliminate it as well as the symptoms everywhere |
| 6. Recovery | Return to normal operations |
| 7. Post Incident Review | Close out the incident and determine areas for improvement |
Analysis, Notification and Escalation
During the analysis phase, the affected City Department coordinates with the City Cyber Defense team, which involves recording available reporting observations, assessing potential incident severity, and determining the type of incident that has occurred. In general, this phase requires the City Cyber Defense team to review playbooks, collect, analyze information, and decide next steps.
This phase has the following goals:
- If necessary, confirm the validity of information provided in the initial lead
- Determine whether the event is a cause for concern or a false positive
- Determine whether further investigation is warranted
- Determine priority of the incident
- Determine need to activate City’s Emergency Operation Center
- Determine immediate Remediation steps
Cyber incidents may be difficult to identify and their impacts not immediately apparent. As a cyber incident develops, timely and flexible coordination is needed to alert and notify key stakeholders. Based on the information provided, additional stakeholders will be identified, and the DEM Director will determine whether the EOC will be activated to a Level II (Partial). If there isn’t a change in the EOC activation level, the City Cyber Defense Team and DEM will establish a timeframe for further briefings.
State and Local Cybersecurity Grant Program
Overview
In September 2022, the federal Department of Homeland Security (DHS) announced the State and Local Cybersecurity Grant Program (SLCGP), established by and funded through the 2022 Infrastructure Investment and Jobs Act (IIJA) to better address cybersecurity risks and threats to information systems of state, local, and territorial governments. SLCGP distributed funds over four federal fiscal years to support projects throughout the period of performance for the program. The DHS Cybersecurity and Infrastructure Security Agency (CISA) and Federal Emergency Management Agency (FEMA) are jointly managing the SLCGP.
As the State Administrative Agency for the SLCGP, Cal OES administers the funds allocated to California through the program and is responsible for ensuring all statutory and programmatic requirements of the fund source are met. To support this effort, Cal OES Grants Management developed a competitive funding application process with a formal notice of Request for Proposals (RFPs). There are separate application processes for the three categories of local government, tribal governments, and state agencies to apply for funding.
State and Local Cybersecurity Grant Program Funds
The first RFP was released on July 31, 2024, using funds from both the FFY 2022 and FFY 2023 SLCGP, and is now closed.
For each of the remaining SLCGP funds, FFY 2024 and FFY 2025, more detailed information and applications are available on the Cal OES Grants Management homepage, Cal OES Grants Management Search for Grants Function, and the California Grants Portal website.
**** The application period for FFY 2024 SLCGP funding is now open. ****
For FFY 2024, $11.5M in SLCGP funds is available to local government agencies, tribal government agencies, and state agencies. Cal OES will be conducting webinars to provide Applicants with technical assistance on the proposal requirements. The FFY 2024 SL and FFY 2024 SG Program RFPs, Notice of Interest (NOI) Forms, and Project Worksheet Forms are available on the Cal OES website.
Proposals must be received by: Friday, March 13, 2026, 11:59 PM (PDT). Submissions received after this deadline will not be considered.
FFY 2024 SLCGP Webinar Schedule
|
Tuesday, February 10, 2026 Webinar 1: (10:00 AM – 12:00 PM) Call In: +1 415-906-4037 Conference ID: 241 941 56# |
Thursday, February 12, 2026 Webinar 2: (1:00 PM – 3:00 PM) Call In: +1 415-906-4037 Conference ID: 653 474 952# |
|
Wednesday, February 18, 2026 Webinar 3: (1:00 PM – 3:00 PM) Call In: +1 415-906-4037 Conference ID: 278 021 065# |
Thursday, February 19, 2026 Webinar 4: (10:00 AM – 12:00 PM) Call In: +1 415-906-4037 Conference ID: 929 111 643# |
The following three (3) proposal documents must be submitted in one email to the following email address: StateLocalProjects@caloes.ca.gov and received by Friday, March 13, 2026, 11:59 PM PDT. A completed proposal must consist of the three required documents attached in a single email.
1. FFY 2024 SL Program NOI Fillable PDF (if Applicant is a local or tribal government) or FFY 2024 SG Program NOI Fillable PDF (if Applicant is an agency of the State of California).
2. FFY 2024 SLCGP Project Worksheet (Excel).
3. Cybersecurity Maturity Survey – PDF copy of the Applicant’s responses to the online survey.
Technical questions pertaining to the FFY 2024 SL or SG Program proposal process can be addressed to the State & Local Projects Unit at StateLocalProjects@caloes.ca.gov.
State and Local Cybersecurity Grant Program (SLCGP) Required Surveys
Applicants are required to complete various surveys – please see the appropriate Request for Proposals for details. Applicants should complete only ONE survey/questionnaire for each organization/agency applying for a grant. Please coordinate within your organization to ensure the appropriate cybersecurity leaders and subject matter experts weigh-in on these surveys, but they can be submitted by your primary grant applicant point of contact.
- REQUIRED: State and Local Government Cybersecurity Maturity Questionnaire
- Survey link: https://calcsic-prod.agilsoft.cloud/worker-portal/public/survey/6d22650d-b333-4e25-941e-e0022aeba105
- Opens: Friday, January 16, 2026
- Closes: Friday, March 13, 2026
- The agilsoft.cloud link provided above is to an approved vendor platform provided under contract to Cal OES. If possible, please save a copy of your organization’s response and include it with your grant application documents. Applicants can also download the questions as a fillable pdf form which may be included with grant applications.
For more information on the SLCGP, see the Cal OES Grants Management SLCGP page.
Note: For SLCGP application process, please go to Grant Announcements | California Governor’s Office of Emergency Services.
For interest in joining or participating in the California Cybersecurity Task Force: Register here.
Mission
The California Cybersecurity Task Force is an advisory body to the State of California Senior Administration Officials in matters related to Cybersecurity.
History and Mandate
From its creation in 2013 until approximately 2018, Cal OES had built the California Cybersecurity Task Force (CCTF) to be the preeminent cybersecurity advisory body for California. After the Cal-CSIC stood up in 2018, it took on the responsibility of running the CCTF. It is composed of seven subcommittees focused on goals and objectives aligned to state cybersecurity objectives. The subcommittees are comprised of subject matter experts and executive representatives from Federal, State, local, and tribal government, private industry, academia, and law enforcement in California.
In accordance with Section 8586.5 of the Government Code:
“The Office of Emergency Services shall establish and lead the California Cybersecurity Integration Center. The California Cybersecurity Integration Center’s primary mission is to reduce the likelihood and severity of cyber incidents that could damage California’s economy, its critical infrastructure, or public and private sector computer networks in our state. The California Cybersecurity Integration Center shall serve as the central organizing hub of state government’s cybersecurity activities and coordinate information sharing with local, state, and federal agencies, tribal governments, utilities and other service providers, academic institutions, and nongovernmental organizations.”
Furthermore:
“The California Cybersecurity Integration Center shall develop a statewide cybersecurity strategy, informed by recommendations from the California Task Force on Cybersecurity and in accordance with state and federal requirements, standards, and best practices. The cybersecurity strategy shall be developed to improve how cyber threats are identified, understood, and shared to reduce threats to California government, businesses, and consumers. The strategy shall also strengthen cyber emergency preparedness and response, standardize implementation of data protection measures, enhance digital forensics and cyber investigative capabilities, deepen expertise among California’s workforce of cybersecurity professionals, and expand cybersecurity awareness and public education.”
How You Can Participate
The CCTF is open to cybersecurity professionals from across the state who are committed to improving cybersecurity in California. It is composed of subject matter experts and executive representatives from Federal, State, local, and tribal government, private industry (particularly utilities and service providers), academia, non-governmental organizations, and law enforcement in California. All CCTF members have a vested interest in cybersecurity, and their involvement and commitment will benefit California and its citizens. As a voluntary organization, you can participate as much or as little as you have time for. By taking an active role in the CCTF you will find opportunity to help shape major cybersecurity initiatives, network with colleagues, share your insights, bring best practices back to your organizations, and learn more about what the Cal-CSIC and its partners are doing to build security in cyberspace. If you are interested in joining, please use the registration link at the top of this page, the contact information below, or the registration link on the side panel.
Subcommittees
Task Force subcommittees have been formed based on strategic goals and vital areas of opportunity. There are nine subcommittees within the Task Force each focused on a specific strategic goal.
Election Security Subcommittee (ESS)
- Strengthen statewide election system security by coordinating information sharing, supporting vulnerability assessments, and advising on best practices across voter registration, management, tabulation, and reporting systems.
- Enhance preparedness through targeted training and exercises and provide ongoing guidance to the Steering Committee on election-related cybersecurity and statutory outreach requirements.
- Subcommittee Chair: Travis Nichols, California Cybersecurity Integration Center
Emerging Technology Subcommittee (ETS)
- Identify and assess cybersecurity risks and opportunities associated with artificial intelligence (AI), machine learning, quantum computing, 5G, IoT, autonomous systems, blockchain, and biotech, while advising on responsible policy and procurement frameworks.
- Coordinate with technology, research, investment, regulatory, and cybersecurity communities and support implementation of major AI-related state statutes and guidance.
Critical Infrastructure Subcommittee (CIS)
- Advise on cybersecurity risks, regulatory issues, OT/ICS security, supply chain vulnerabilities, sector interdependencies, and strategies for protecting legacy systems.
- Promote resilience and shared situational awareness through collaboration among owners/operators, regulators, sector councils, and experts, including enhanced threat information sharing and recovery planning.
Cyber Risk Management Subcommittee (CRMS)
- Strengthen statewide cyber readiness through comprehensive risk frameworks, best-practice guidance, incident response alignment with national standards, and governance of risk across agencies and critical infrastructure.
- Support resilience planning and develop metrics to measure cyber posture, business continuity, disaster recovery, and long-term capability improvements.
- Subcommittee Chair: MAJ Massimo Rapparini, CA Army National Guard
Workforce Development and Education Subcommittee (WDES)
- Align and strengthen cybersecurity education pathways and expand the talent pipeline through partnerships across K-12, higher education, vocational programs, and industry certification providers.
- Advance statewide workforce readiness through awareness, upskilling, and coordinated development initiatives that support government, critical infrastructure, small businesses, and broader economic and equity goals.
- Subcommittee Chair: Dr. Keith Clement, CSU Fresno
High Tech and Digital Forensics Subcommittee (HTDFS)
- Develop statewide digital evidence training and readiness frameworks for law enforcement and non-law enforcement responders, including mutual aid agreements for evidence acquisition and preservation.
- Build regional digital forensics capacity covering cloud, IoT, mobile, cryptocurrency, and AI investigations through expanded laboratory capabilities and specialized expertise.
Training and Exercise Subcommittee (TES)
- Design and coordinate cybersecurity training, tabletop exercises, functional exercises, and full-scale simulations to strengthen preparedness, interagency coordination, and leadership decision-making.
- Lead annual statewide exercises, develop playbooks and training resources, and establish metrics to evaluate communication, coordination, capability gaps, and overall multi-agency response readiness.
- Subcommittee Chair: Matthew Ivler, California Cybersecurity Integration Center
Cybersecurity Investment Planning Subcommittee (CIPS)
- Recommend strategic cybersecurity investment priorities, monitor the effectiveness of grant-funded initiatives, and provide guidance to agencies and applicants on available cybersecurity grants.
- Serve as the required State and Local Cybersecurity Grant Program planning committee and facilitate information sharing among eligible state, local, tribal, special district, and educational entities to maximize statewide impact.
Economic Development Subcommittee (EDS)
- Expand California’s cybersecurity industry by advising on research, innovation, asset development, and integration of cybersecurity into regional and statewide economic strategies.
- Support international engagement and market access for California cybersecurity companies while ensuring compliance with export controls and safeguarding sensitive technologies.
Contact Information
Questions regarding CCTF, or to be added to the Contact List:
Email calcsic@caloes.ca.gov
Put [California Cybersecurity Task Force inquiry] in subject line
If requesting to be added to the contact list, please use your work email and include your organization, position/title, and cybersecurity role
If interested in Joining or Participating in the CCTF:
Register here.
Cybersecurity Investment Planning Subcommittee & SLCGP:
Request to join the CCTF CIPS and be added to the distro: cctf-slcgp@caloes.ca.gov
Questions about SLCGP: StateLocalProjects@caloes.ca.gov
Attention California Public School Districts, County Offices Of
Education, & Charter Schools:
See information below for Reporting Cyberattacks
Cal-CSIC AB2355 Flyer – How To Report A Cyberattack
Report cyber incidents to the Cal-CSIC at (916) 636-2997 or calcsic@caloes.ca.gov.
Subscribe to Alerts, Advisories, and Product Distribution
Email: calcsic@caloes.ca.gov
Training and Awareness Program
State, local, and tribal governments, non-governmental organizations and the private sector can partner with the Cal-CSIC by registering to receive Alerts and Advisories, sharing IOCs and cyber incident reports, and connecting to the California Automated Indicator Exchange.
Email the Cal-CSIC to learn more about sharing of IOCs and connecting to the California Automated Indicator Exchange at calcsic@caloes.ca.gov.
Report cyber incidents to the Cal-CSIC at (916) 636-2997 or calcsic@caloes.ca.gov.
If interested in Joining or Participating in the CCTF:
Register here.
