California Cybersecurity Integration Center

The California Cybersecurity Integration Center’s primary mission is to reduce the likelihood and severity of cyber incidents that could damage California’s economy, its critical infrastructure, or public and private sector computer networks in our state.
- About Cal-CSIC
- Organization
- ESF 18
- Cal-Secure
- Cal-CSIC Commander
- Cybersecurity Surveys
- California Cybersecurity Task Force
Mission
The California Cybersecurity Integration Center’s (Cal-CSIC) mission is to reduce the number of cyber threats and attacks in California. The Cal-CSIC’s focus is to respond to cyber threats and attacks that could damage the economy, its critical infrastructure, or computer networks in the state.
The Cal-CSIC is the hub of state government’s cybersecurity events. The Cal-CSIC will coordinate information sharing at all levels of government agencies, utilities and other service providers, academic institutions, and nongovernmental organizations.
The Cal-CSIC will publish a statewide cybersecurity strategy. The strategy will take recommendations from the California Task Force on Cybersecurity and follow state and federal requirements. The cybersecurity strategy will improve how cyber threats are found, understood, and shared. The strategy will strengthen cyber emergency preparedness and response, standardize data protection measures, enhance digital forensics, and increase cyber investigative capabilities, supply lessons learned to California’s workforce of cybersecurity professionals, and expand cybersecurity awareness.
The Cal-CSIC will supply a Cyber Incident Response Team to serve as California’s primary unit to lead cyber threat detection, reporting, and response to public and private entities across the state.
The Incident Response Team will aid law enforcement agencies with jurisdiction for cyber-related criminal investigations and work with agencies responsible for advancing information security within state government.
Cal-CSIC information sharing will protect the privacy and civil liberties of individuals and preserve business confidentiality. Cal-CSIC will publish Cyber Threat Alerts and Advisories that will supply cybersecurity threat information between Federal, State, Local, and Tribal government entities. Advisories and Alerts are shared with private sector partners.
Cal-CSIC Analysts will collect and analyze phishing emails to document relevant information about the attacker and the Indicators of Compromise (IOC). These IOCs are added to the California Automated Indicator Exchange and is accessible to all partner entities.
The California Cybersecurity Integration Center is composed of 3 branches that mutually support the Commander’s mission.
Cyber Operations Branch Services
- Incident Response
- Reactive
- Rapid Response
- Threat Identification
- Threat Containment
- Threat Eradication
- Rapid Response
- Proactive
- Security Assessments
- Network Perimeter Vulnerability Scan
- Dark Web Review (Credentials & Data Dumps)
- Net Flow Traffic Analysis
- Free 30-Day License for an Endpoint Detection and Remediation Tool
- Security Assessments
- Reactive
- Digital Forensics
- Hard Disk Forensics
- Memory Forensics
- Network Forensics
- Malware Analysis
Cyber Threat Intelligence Services
- Tactical
- Intelligence Collection and Analysis
- Intelligence Aggregation
- Intelligence Origination
- Cyber Threat Analysis
- Intelligence Governance
- Vulnerability Analysis
- Attack Surface Reduction
- Network Footprinting
- Cyber Risk Analysis
- Prioritized Vulnerability Reporting
- Critical Vulnerability Patch Validation
- Intelligence Collection and Analysis
- Strategic
- Planning and Coordination
- Dissemination
- Intelligence Objective Prioritization
- Intelligence Collection Planning
- Planning and Coordination
Mission Support Branch Services
- Digital Forensics
- Cyber Policy and Strategy Generation
- Knowledge Management
- Vendor Management
- Product Support
- Relationship Management
- Partner Integration
- Onboarding and Partner Success
- IT Engineering
- IT Project Management
- System Engineering and Development
- Metrics Collection and Reporting
- IT/Cyber Investment Management
- Metrics Reporting and Governance
The purpose of this Emergency Support Function (ESF) #18: Unified Cyber Command Annex is the following:
- establish a unified understanding of key cyber concepts and terminologies
- provide a system to evaluate the severity of a cyber incident
- assign roles and responsibilities to City stakeholders
The plan is specifically focused on priority SEVERE or EMERGENCY cyber incidents, when the City’s Emergency Operations Center (EOC) is activated to coordinate:
- key processes for sharing threat intelligence
- develops situational awareness
- manages operational response in a cyber- disrupted environment
Scope
ESF #18: Unified Cyber Command Annex plan addresses cyber incidents that have or could potentially degrade, damage, or destroy information systems in City Departments, Agencies, Offices, and Commissions. High focus will be given to cyber incidents affecting City government critical functions and infrastructure, including:
- Medical/Healthcare Services
- Government/Public Safety Services
- Financial/Banking Services
- Transportation/Transit Services
- City’s Telecommunications Services
- City’s managed Lifelines – Critical Infrastructure
- City’s Radio Infrastructure
- City and Department IT Networks
- City and Department Enterprise Technology and Applications
Unified Cyber Command Incident Response Process
| Phase | Objective |
|---|---|
| 1. Preperation | Identify activity or work that should be completed to make the response successful |
| 2. Reporting and Detection | Provide channel to report suspected incidents and verify that an incident has occured |
| 3. Analysis, Notification and Detection | Understand the incident and begin notifications and escalations |
| 4. Containment | Stop the incident from spreading further and eliminate further damage |
| 5. Eradication | Determine the root cause and fully eliminate it as well as the symptoms everywhere |
| 6. Recovery | Return to normal operations |
| 7. Post Incident Review | Close out the incident and determine areas for improvement |
Analysis, Notification and Escalation
During the analysis phase, the affected City Department coordinates with the City Cyber Defense team, which involves recording available reporting observations, assessing potential incident severity, and determining the type of incident that has occurred. In general, this phase requires the City Cyber Defense team to review playbooks, collect, analyze information, and decide next steps.
This phase has the following goals:
- If necessary, confirm the validity of information provided in the initial lead
- Determine whether the event is a cause for concern or a false positive
- Determine whether further investigation is warranted
- Determine priority of the incident
- Determine need to activate City’s Emergency Operation Center
- Determine immediate Remediation steps
Cyber incidents may be difficult to identify and their impacts not immediately apparent. As a cyber incident develops, timely and flexible coordination is needed to alert and notify key stakeholders. Based on the information provided, additional stakeholders will be identified, and the DEM Director will determine whether the EOC will be activated to a Level II (Partial). If there isn’t a change in the EOC activation level, the City Cyber Defense Team and DEM will establish a timeframe for further briefings.
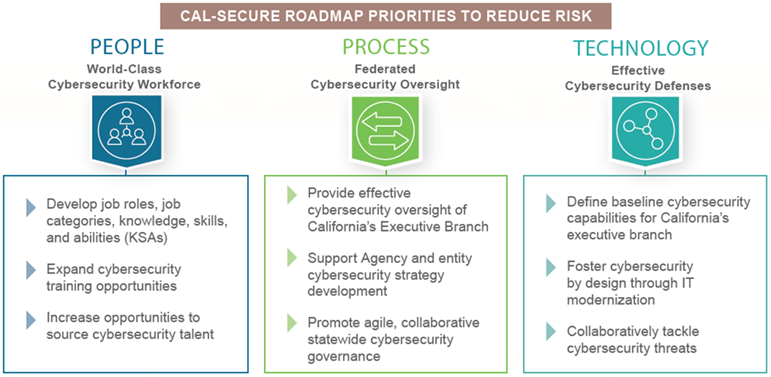
In early October 2021, The California Department of Technology (CDT) announced Cal-Secure. At its core, Cal-Secure is a five-year information security roadmap designed to increase cyber resiliency amongst California State Agencies. It implements a process that results developing a world-class cybersecurity workforce. This effort will bring people, processes, and technologies together in a joint and cohesive effort to increase the cybersecurity protective posture for the State of California.
Cal-CSIC Commander (Vacant)
Current duties of the Cal-CSIC Commander include:
- Work with multi-jurisdictional stakeholders
- Manage interdisciplinary teams charged with safeguarding information technology assets and cyber networks.
- Maintain in-depth knowledge of state-of-the-art cyber defense strategies and mitigation efforts, including hardware and software, and network protection configurations.
- Maintain knowledge of homeland security strategies, particularly with respect to California, and their interrelationship with cyber security policy
- Develop and execute Budget Change Proposals
Overview
This page hosts several surveys relevant to cybersecurity in California. In general, participation is voluntary. However, select surveys may be requirements for grant program subrecipients.
State and Local Cybersecurity Grant Program (SLCGP) Required Surveys
Please complete only ONE survey/questionnaire for each organization/agency applying for a grant. Duplicates may be ignored. Please coordinate within your organization to ensure the appropriate cybersecurity leaders and subject matter experts weigh in on these surveys, but they can be submitted by your primary grant applicant point of contact.
- REQUIRED: Local Government Cybersecurity Maturity Questionnaire (closes June 26, 2024)
- The link above is via the Microsoft Office.com platform provided under contract to Cal OES. Please save a copy of your response if you can and include with your grant application documents. If you would prefer to complete this more directly, you can download the questions (PDF). In both cases, send the completed form to InternalProjects@caloes.ca.gov with your grant application documents.
- REQUIRED: Desired Cybersecurity Services Survey (closes June 26, 2024)
- REQUIRED: See NCSR below. The NCSR is a post-award requirement for SLCGP sub-recipients.
For more information on the SLCGP, see the Cal OES Grants Management SLCGP page
NCSR
The Nationwide Cybersecurity Review (NCSR) is generally voluntary but is also a requirement of certain federal grant programs. The NCSR is a free, anonymous, annual self-assessment designed to measure gaps and capabilities of a SLT’s cybersecurity programs. It is based on the National Institute of Standards and Technology Cybersecurity Framework and is sponsored by DHS and the MS-ISAC.
SLCGP entities and their subrecipients should complete the NCSR, administered by the MS-ISAC, during the first year of the award/subaward period of performance and annually.
For more information, visit Nationwide Cybersecurity Review (NCSR) (cisecurity.org).
Mission
The California Cybersecurity Task Force is an advisory body to the State of California Senior Administration Officials in matters related to Cybersecurity.
History and Mandate
From its creation in 2013 until approximately 2018, Cal OES had built the California Cybersecurity Task Force (CCTF) to be the preeminent cybersecurity advisory body for California. After the Cal-CSIC stood up in 2018, it took on the responsibility of running the CCTF. It is composed of seven subcommittees focused on goals and objectives aligned to state cybersecurity objectives. The subcommittees are comprised of subject matter experts and executive representatives from Federal, State, local, and tribal government, private industry, academia, and law enforcement in California.
In accordance with Section 8586.5 of the Government Code:
“The Office of Emergency Services shall establish and lead the California Cybersecurity Integration Center. The California Cybersecurity Integration Center’s primary mission is to reduce the likelihood and severity of cyber incidents that could damage California’s economy, its critical infrastructure, or public and private sector computer networks in our state. The California Cybersecurity Integration Center shall serve as the central organizing hub of state government’s cybersecurity activities and coordinate information sharing with local, state, and federal agencies, tribal governments, utilities and other service providers, academic institutions, and nongovernmental organizations.”
Furthermore:
“The California Cybersecurity Integration Center shall develop a statewide cybersecurity strategy, informed by recommendations from the California Task Force on Cybersecurity and in accordance with state and federal requirements, standards, and best practices. The cybersecurity strategy shall be developed to improve how cyber threats are identified, understood, and shared to reduce threats to California government, businesses, and consumers. The strategy shall also strengthen cyber emergency preparedness and response, standardize implementation of data protection measures, enhance digital forensics and cyber investigative capabilities, deepen expertise among California’s workforce of cybersecurity professionals, and expand cybersecurity awareness and public education.”
How You Can Participate
The CCTF is open to cybersecurity professionals from across the state who are committed to improving cybersecurity in California. It is composed of subject matter experts and executive representatives from Federal, State, local, and tribal government, private industry (particularly utilities and service providers), academia, non-governmental organizations, and law enforcement in California. All CCTF members have a vested interest in cybersecurity and their involvement and commitment will benefit California and its citizens. As a voluntary organization, you can participate as much or as little as you have time for. By taking an active role in the CCTF you will find opportunity to help shape major cybersecurity initiatives, network with colleagues, share your insights, bring best practices back to your organizations, and learn more about what the Cal-CSIC and its partners are doing to build security in cyberspace. If you are interested in joining, please use the contact information below.
Subcommittees
Task Force subcommittees have been formed based on strategic goals and vital areas of opportunity. There are seven subcommittees within the Task Force each focused on a specific strategic goal.
Workforce Development & Education Subcommittee (WDES)
- Recommend alignment and refinement of the cybersecurity educational pathways inclusive of curricula, competitions, and professional development activities at the high school level of education and higher. There will be focus on ensuring veterans and the underrepresented in the field of cybersecurity are included and are afforded opportunities.
- Subcommittee Chair: Dr. Keith Clement, CSU Fresno
Cyber Risk Management Subcommittee (CRMS)
- Enhance California’s ability to detect, protect against, mitigate, respond to, and recover from significant cyber incidents.
- Build public and private partnerships to support and ensure relationships that establish and guarantee the success of the subcommittee.
- Advise on best practices to identify, mitigate, and govern cyber risk across the State.
Critical Infrastructure Subcommittee (CIS)
- Provide recommendations for cybersecurity protection, prevention, detection, and response for critical infrastructure in the State.
- Critical Infrastructure is defined by FEMA and Cal OES, but the Critical Infrastructure Subcommittee should take an active role in helping refine those definitions including risk assessment methodologies.
- Provide a forum for advising the Cal-CSIC on critical infrastructure issues related to state and federal legislation and regulatory frameworks/proposals, and to facilitate outreach required by these statutes and regulations
Information Sharing Subcommittee (ISS)
- Develop information sharing agreements and best practices, for the purposes of enhancing threat detection, providing early warnings of cyberattacks, and assessing risk to the State.
- Exercise cyber information sharing capabilities annually and encourage responsible cyber threat information sharing and reporting.
High Tech & Digital Forensics Subcommittee (HTDFS)
- Advise and assist with a framework for developing a digital evidence training program and State law and non-law enforcement readiness to respond to cybersecurity incidents.
- Establish law enforcement mutual aid agreements for the acquisition and preservation of digital evidence in conjunction with the California Highway Patrol and the FBI’s Cyber Task Force.
Economic Development Subcommittee (EDS)
- Advise on ways to expand research and innovation in cybersecurity industries in California.
- Advise on ways to expand California’s cybersecurity assets to attract additional investment into the state.
Cybersecurity Investment Planning Subcommittee (CIPS)
- Will directly advise and assist in development of the state cybersecurity strategy
- Will advise on cybersecurity grant programs available in California in coordination with other relevant subcommittees, and facilitate information sharing with potential grant recipients
- In 2022 the Cal-CSIC formed the seventh subcommittee of the CCTF called the Cybersecurity Investment Planning Subcommittee to serve as the “planning committee” required by the State and Local Cybersecurity Grant Program (SLCGP). SLCGP is a component of the 2021 federal Infrastructure Investment and Jobs Act (IIJA) also known as the Bipartisan Infrastructure Law.
- CCTF-CIPS is limited to all potential grant recipients (state and local governments, special districts, school districts, tribal governments, etc. as defined in SLCGP) and their designated representatives.
- In 2023, the CCTF-CIPS overseen by the Cal-CSIC produced the first-year SLCGP Cybersecurity Plan, which is posted here: California’s SLCGP Cybersecurity Plan v1.5.5 (September, 2023)
- To apply for SLCGP funds as a subrecipient, please go to the Cal OES Grants Management SLCGP page
Contact
CCTF Questions, To Join, Or To Be Added To Contact List:
- Put [California Cybersecurity Task Force inquiry] in subject line
- calcsic@caloes.ca.gov
Cybersecurity Investment Planning Subcommittee & SLCGP:
- Request to join the CCTF CIPS and be added to the distro: cctf-slcgp@caloes.ca.gov
- Questions about SLCGP: InternalProjects@caloes.ca.gov
State, local, and tribal governments, non-governmental organizations and the private sector can partner with the Cal-CSIC by registering to receive Alerts and Advisories, sharing IOCs and cyber incident reports, and connecting to the California Automated Indicator Exchange.
Email the Cal-CSIC to learn more about sharing of IOCs and connecting to the California Automated Indicator Exchange at calcsic@caloes.ca.gov.
Report cyber incidents to the Cal-CSIC at (833) REPORT-1 or calcsic@caloes.ca.gov.

